Key Takeaways:
- Cozentus ensures you own 100% of your IP. From code to design, with clear contracts and clean handovers.
- Secure development practices ensure your data, assets, and code stay protected at every stage.
- Role-based access, isolated environments, and detailed audit trails help clients maintain full control over their IP.
- Dedicated teams, strict access controls, and full transparency provide you with peace of mind as you scale quickly.
Work with External Teams and Keep Your IP Safe
For most businesses, a lack of intellectual property (IP) protection is the deal-breaker. Your product idea, codebase, algorithms, and years of business knowledge are your intellectual property (IP), and they are valuable. But the moment you involve an external partner to help you build or scale, this basic question pops up:
"Will my IP still be mine?"
We understand this concern because we hear it all the time, especially when legal or procurement teams join the conversation.
At Cozentus, we address this head-on. Our clients include tech-first startups and Fortune 500s, and across the board, their message is the same: "We want speed and innovation, but not at the cost of control."
We’ve designed our delivery models, contracts, and teams to support just that.

The Real Risk: Why IP Protection Matters
Let’s address the elephant in the room. Why does IP risk even arise in outsourced or co-built models?
- Codebase leakage: When multiple developers or vendors work on a product, it becomes hard to control where the code lives, who accesses it, and how it's used later.
- Reused components: Some vendors reuse your code or architecture patterns with different clients, knowingly or unknowingly. This leads to serious IP conflicts.
- Third-party dependencies: Unvetted open-source packages or SaaS integrations can become a door for legal or security liabilities.
- Contractual gray areas: Many service agreements leave loopholes around ownership, licensing rights, or future usage.
At Cozentus, we solve these pain points head-on. Let’s dive into how.
What You Own
Everything we build for you is fully yours.
From source code and product designs to architecture diagrams and deployment scripts, you retain 100% IP ownership. There are no shared licenses, no reuse clauses, and no fine print.
Our contracts clearly state:
- You own all outputs from day one.
- No part of your IP will be reused, shared, or referenced in other client work.
- All work is developed in your repositories or cloud environment.
This is true whether you're building a new product, augmenting your team, or using us for rapid prototyping.
What We Sign
We make legal teams comfortable, not cautious.
We know many partnerships slow down or stall when procurement or legal departments step in. So, we ensure our paperwork makes things easy for them.
Here’s how we do that:
- Crystal-clear contracts with no confusion about ownership, licensing, or reuse.
- Individual NDAs signed by every developer, tester, and project manager assigned to your work.
- Compliance-ready terms that align with your internal legal, procurement, and governance standards.
If your legal team needs specific clauses or security provisions, we collaborate to make sure every concern is addressed up front.
Why It Works
Our model isn’t just secure on paper. It’s designed for real-world IP protection.
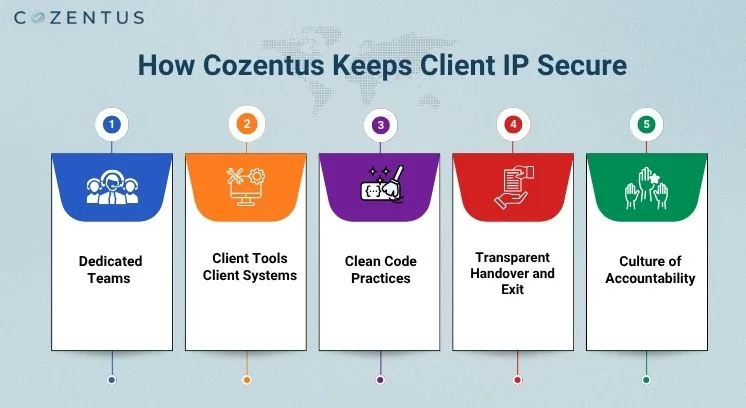
1. Dedicated Teams Only for You
We don’t share resources across clients. Your project gets a dedicated team that works only on your objectives, including developers, architects, and QA engineers. This keeps your information safe, helps the team get started quickly, and makes everyone clearly responsible for the work they do. They adopt your culture, tools, and way of working to act like an extension of your in-house team.
2. Your Tools - Your Systems
All development happens within your infrastructure, your cloud environment, your GitHub account, and your VMs. Nothing is developed or stored outside your ecosystem. We implement strict role-based access control, regular permission audits, and time-bound credentials to ensure complete visibility and traceability.
3. Clean Code Practices
Speed should never come at the cost of safety. That’s why we apply automated and manual reviews to make sure all code is clean, licensed appropriately, and secure. Even third-party library or open-source components is checked for compatibility, licensing, and security posture before use. This helps in avoiding long-term legal or technical debt.
4. Transparent Handover and Exit
From day one, we prepare for a clean and complete exit. All deliverables, from code and test cases to architecture maps and API documentation, are handed over systematically. Credentials are revoked on the same day. We also share a closure report with full access logs, tools that we used, and version histories to ensure you retain total control.
5. Culture of Accountability
Security and trust are part of our team culture. Everyone at Cozentus is trained on IP protocols, ethical engineering, and client confidentiality. It’s not just policy, it’s a mindset. Our teams know the value of your IP and treat it with the seriousness it deserves, with zero tolerance for oversight or misuse.
What Big Tech Gets Right (And How We Apply It)
Companies like Apple, Microsoft, and other tech giants work with hundreds of third-party vendors. Yet they never compromise on control.
They do it through:
- Strict rules for working with partners
- Dedicated teams with signed NDAs
- Development inside private systems
At Cozentus, we follow the same principles. We follow the same approach that top enterprises use to work with multiple partners, while keeping their IP fully protected.
Read: From Project Rescue to Product Launch: The Cozentus Approach
The Industry Reality
According to a Capgemini Research Institute study, over 70% of companies consider IP risk a top concern when outsourcing or using offshore vendors.
Gartner predicts that by 2026, many companies will slow down their use of generative AI because of the rising costs and risks of protecting intellectual property and avoiding copyright problems. This will lead to lower returns on their AI investments.
That’s why our model is built to prevent:
- Unauthorized access
- Legal ambiguity
- Code leakage
- Component misuse
Because in this environment, secure delivery is not optional, but essential.
Bottom Line: Grow without Risk
We believe that outsourcing or augmenting your tech team should accelerate your growth, not create risk.
With Cozentus, you get:
- Full IP ownership, always.
- Clear contracts and full compliance.
- Secure systems and accountable teams.
So yes, you can work with an external partner without compromising on your IP. Thousands of businesses already do it the right way. And we help them do it better.
Let’s talk if you’re ready to keep your IP and grow securely.
Recent Post
Subscribe to our newsletter
Stay updated on latest trends and news in the supply chain and logistics industry
Join our mailing list for monthly updates
Download Reports
AI-Powered Intelligent Document Processing -Your Launchpad to Digital Transformation
Download